The Godfather enters: banking Trojan targets users of more than 400 apps in 16 countries

Group-IB, one of the global cybersecurity leaders, presented its findings about Godfather, an Android banking Trojan that is currently being utilized by cybercriminals to attack users of leading banking and crypto exchange applications in 16 countries. As of October 2022, 215 banks, 94 crypto wallet providers, and 110 crypto exchange platforms have been targeted by Godfather.
To date, Godfather has targeted the users of more than 400 applications thanks to its ability to generate convincing web fakes and overlay them on the screens of infected devices when a user tries to open a targeted application. With this scheme, the threat actors leveraging Godfather attempt to steal victims’ login credentials and bypass two-factor authentication in order to gain access to victims’ accounts and drain their funds. During their research into this new Android Trojan, Group-IB’s Threat Intelligence team discovered that Godfather is a successor of Anubis, a widely-used banking Trojan whose functionalities were limited by Android updates and the prior efforts of malware detection and prevention providers.
It’s not personal, it’s strictly business
As of October 2022, 215 banks, 94 crypto wallet providers, and 110 crypto exchange platforms have been targeted by Godfather. The Trojan has also been used in a range of markets, as users in more than a dozen countries have been at risk of having their credentials stolen by threat actors leveraging Godfather. According to Group-IB’s findings, banking applications in the United States (49 companies), Turkey (31), Spain (30), Canada (22), France (20), Germany (19), and the United Kingdom (17), have been the most targeted by this particular Trojan. A full breakdown of Godfather’s scope can be found below:
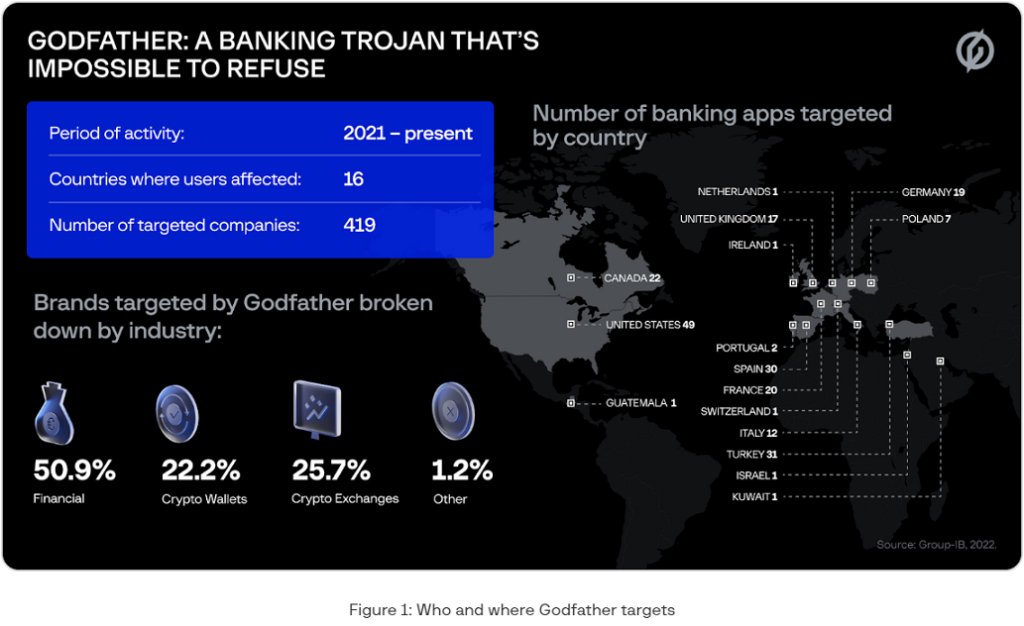
Interestingly, Group-IB found in Godfather’s code a functionality that stops the Trojan from attacking users who speak Russian or one of a number of languages used in the former Soviet Union, which could suggest that the developers of Godfather are Russian speaking. The Trojan does this by checking the system language of the infected device and shutting down if the language is one of: Russian, Azerbaijani, Armenian, Belarusian, Kazakh, Kyrgyz, Moldovan, Uzbek, or Tajik.
Once Godfather is downloaded onto a device, the Trojan attempts to achieve persistence by imitating Google Protect, a legitimate program that runs once an individual downloads an application from the Play Store. The malware is able to emulate the legitimate Google application and indicates to the user that it is “scanning”. However, the malware is doing nothing of the sort. Instead, it creates a pinned “Google Protect” notification and hides its icon from the list of installed applications.
The malware, as “Google Protect”, also launches a service to request access to AccessibilityService, an Android feature used by developers to adapt their applications to users with disabilities. Access to AccessibilityService is also requested once the user presses the “Scan” button in the fake Google Protect application. With access to AccessibilityService, Godfather issues itself the necessary permissions and starts communicating with the C&C server.
Just when you thought you were out, Godfather pulls you back in
The user, who has no idea that their device is now infected with malware, goes about their daily business. At this point, Godfather kicks into action. A signature feature of Godfather, as with many other banking Trojans, is the use of web fakes, also known as HTML pages created by threat actors that display over legitimate applications. The user may interact with these web fakes at two stages: either when they open a legitimate application that is targeted by Godfather, or when they interact with a decoy notification spoofing a targeted banking or crypto application on the user’s device
The web fakes mimic the login pages for the legitimate applications, and all data that is entered into the fake HTML pages, such as usernames and passwords, is exfiltrated to C&C servers. The threat actors harvest these credentials and then use them to enter the legitimate applications, with the help of Godfather’s functionality to exfiltrate push notifications to harvest two-factor authentication codes, and drain the user’s accounts. While Group-IB does not have definitive data on the amount of money stolen by operators of Godfather, the methods harnessed by malicious actors are cause for concern.
More details here
Anders Olofsson – former Head of Payments Finastra
Banking 4.0 – „how was the experience for you”
„So many people are coming here to Bucharest, people that I see and interact on linkedin and now I get the change to meet them in person. It was like being to the Football World Cup but this was the World Cup on linkedin in payments and open banking.”
Many more interesting quotes in the video below:










