Crooks use progressive web apps for new phishing scam to target customers of banks in Eastern Europe

ESET analysts dissect a novel phishing method tailored to Android and iOS users
An article written by Jakub Osmani – Penetration Tester at ESET- Master’s in Computer Security at FIT CTU
In this blogpost we discuss an uncommon type of phishing campaign targeting mobile users and analyze a case that we observed in the wild that targeted clients of a prominent Czech bank. This technique is noteworthy because it installs a phishing application from a third-party website without the user having to allow third-party app installation. For iOS users, such an action might break any “walled garden” assumptions about security. On Android, this could result in the silent installation of a special kind of APK, which on further inspection even appears to be installed from the Google Play store.
The phishing websites targeting iOS instruct victims to add a Progressive Web Application (PWA) to their home-screens, while on Android the PWA is installed after confirming custom pop-ups in the browser. At this point, on both operating systems, these phishing apps are largely indistinguishable from the real banking apps that they mimic. PWAs are essentially websites bundled into what feels like a standalone application, with this feeling being enhanced by the usage of native system prompts. PWAs, just like websites, are cross-platform, explaining how these PWA phishing campaigns can target both iOS and Android users.
This technique was first disclosed by CSIRT KNF in Poland in July 2023 and, in November 2023, observed in Czechia by ESET analysts working on the Brand Intelligence service. We also observed two cases of mobile campaigns against banks outside of Czechia: one case targeting the Hungarian OTP Bank and another targeting the Georgian TBC Bank.
Overview
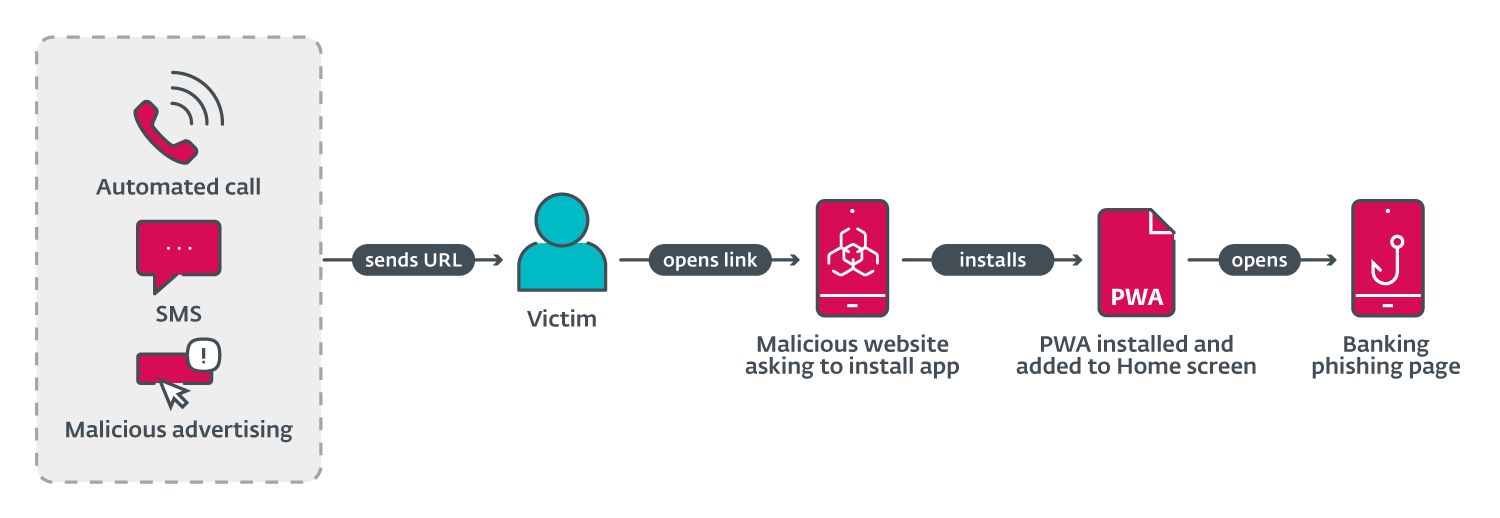
ESET analysts discovered a series of phishing campaigns targeting mobile users that used three different URL delivery mechanisms (shown in Figure 1). These mechanisms include automated voice calls, SMS messages, and social media malvertising.
The voice call delivery is done via an automated call that warns the user about an out-of-date banking app and asks the user to select an option on the numerical keyboard. After pressing the correct button, a phishing URL is sent via SMS. This was reported in a tweet, by Michal Bláha.
Initial delivery by SMS was performed by sending messages indiscriminately to Czech phone numbers. The message sent included a phishing link and text to socially engineer victims into visiting the link.
Spreading via malicious ads was done by registering advertisements on Meta platforms like Instagram and Facebook. These ads included a call to action, like a limited offer for users who “download an update below”. This technique allows threat actors to specify the target audience by age, gender, etc. The advertisements would then appear in a victim’s social media feed.
After opening the URL delivered in the first stage, Android victims are presented with a high-quality phishing page imitating the official Google Play store page for the targeted banking application, or a copycat website for the application. These were two distinct campaigns. It is possible that the campaign utilizing Google Play visuals would modify itself based on the received User-Agent, to imitate Apple Store visuals. We did not observe this technique in analyzed cases.
Figure 1
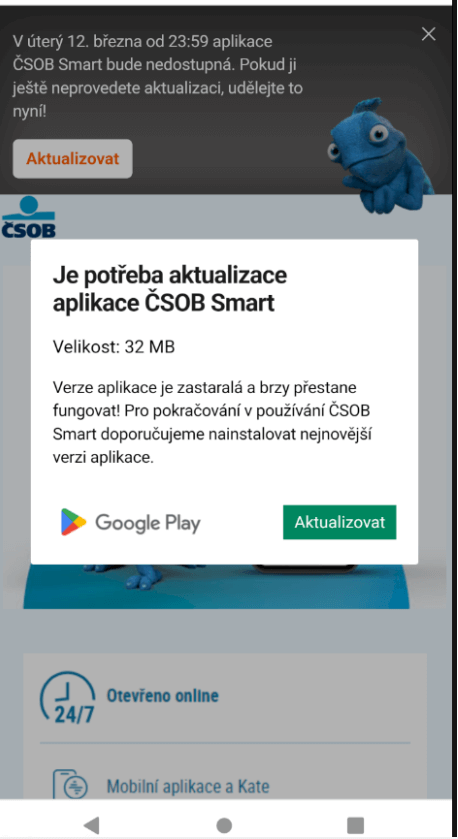
From here victims are asked to install a “new version” of the banking application; an example of this can be seen in Figure 2. Depending on the campaign, clicking on the install/update button launches the installation of a malicious application from the website, directly on the victim’s phone, either in the form of a WebAPK (for Android users only), or as a PWA for iOS and Android users (if the campaign is not WebAPK based). This crucial installation step bypasses traditional browser warnings of “installing unknown apps”: this is the default behavior of Chrome’s WebAPK technology, which is abused by the attackers.
Figure 2
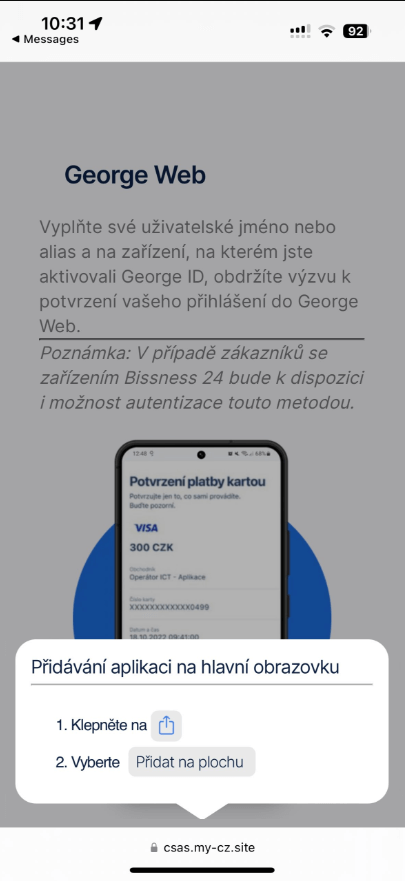
The process is a little different for iOS users, as an animated pop-up instructs victims how to add the phishing PWA to their home screen (see Figure 3). The pop-up copies the look of native iOS prompts. In the end, even iOS users are not warned about adding a potentially harmful app to their phone.
Figure 3
After installation, victims are prompted to submit their internet banking credentials to access their account via the new mobile banking app. All submitted information is sent to the attackers’ C&C servers.
The full article here
Dariusz Mazurkiewicz – CEO at BLIK Polish Payment Standard
Banking 4.0 – „how was the experience for you”
„To be honest I think that Sinaia, your conference, is much better then Davos.”
Many more interesting quotes in the video below:












